3-D Secure
Introduction
When using our Gateway and Fiserv as the 3-D Secure provider, the authentication is performed in-line with the existing transaction flow. The process starts by performing a typical authorization or sale request with a desire to perform 3-D Secure authentication in the request.
The authorization is then placed into a WAITING status until the authentication process is completed. During authentication, the merchant may be required to update the original transaction request one or more times in order to move the process flow forward.
At the end of the authentication process, the original transaction is updated with the authentication results and the authorization is completed.
The sequence diagrams below map to the steps in the text that follows. The first diagram is for the frictionless flow. This means the issuer does not require the cardholder to authenticate.
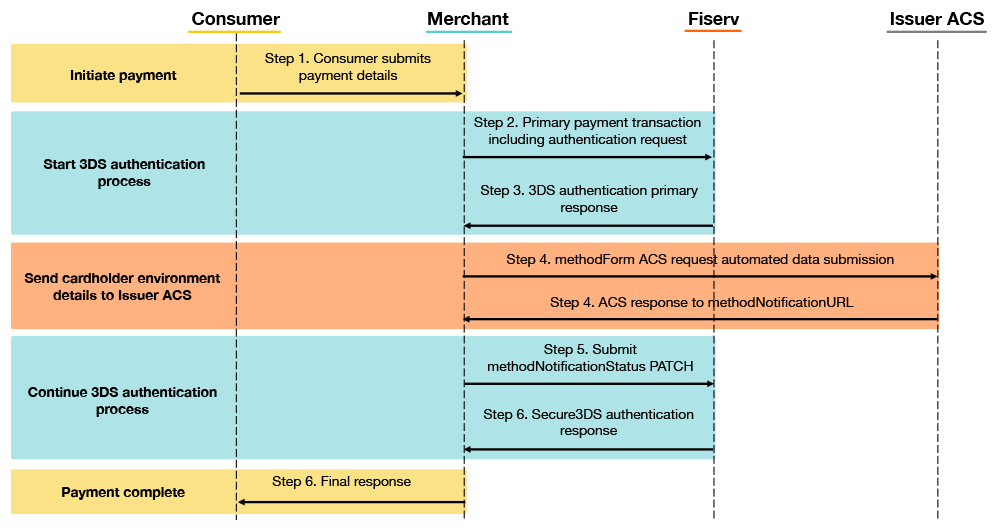
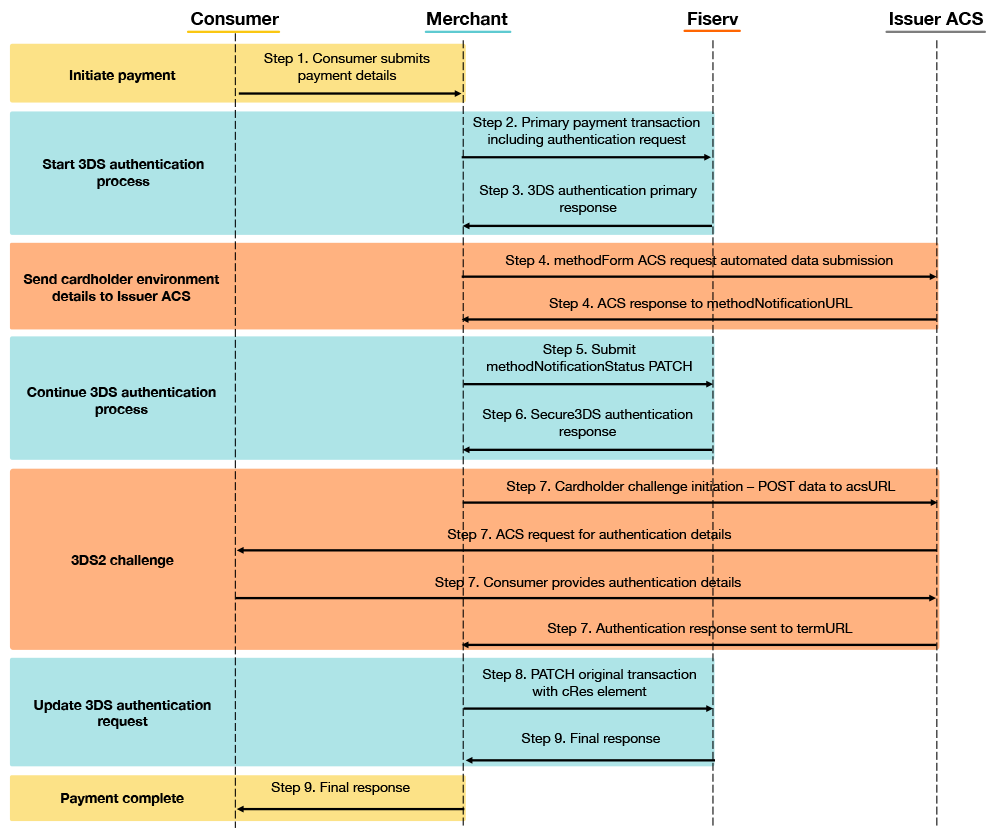
The next diagram shows the flow when your customer has to authenticate, which means their issuer has requested they provide additional authentication details.
REST API Integration
RESTful Payment API solution specifics can be found here: REST API 3DS Integration
SOAP API Integration
SOAP API solution specifics can be found here: SOAP API 3DS Integration
Hosted Payment Page Integration
Hosted Payment Page (Connect) solution specifics can be found here: HPP 3DS Integration
Updated 12 months ago